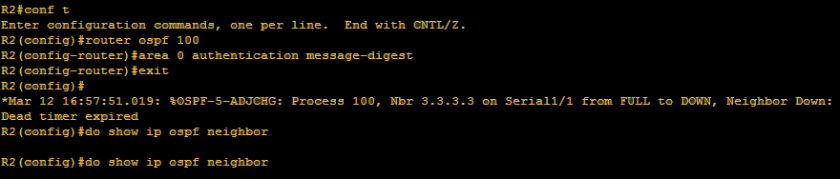
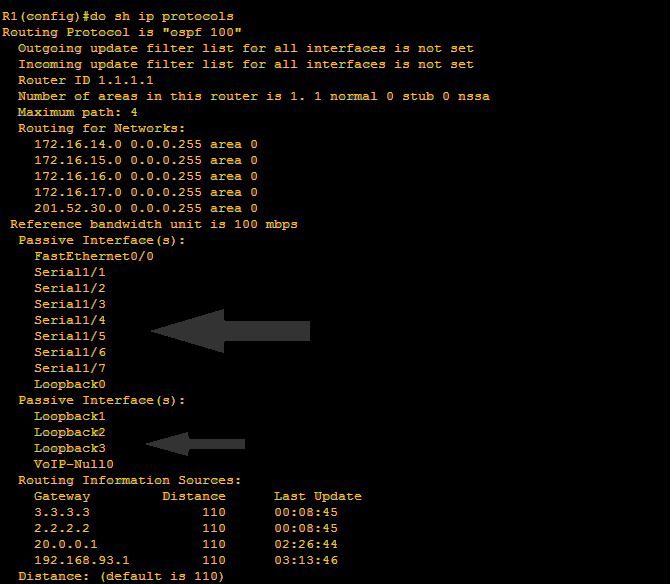
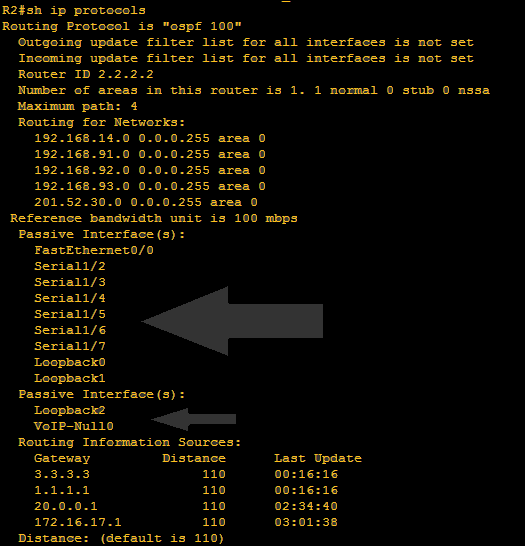
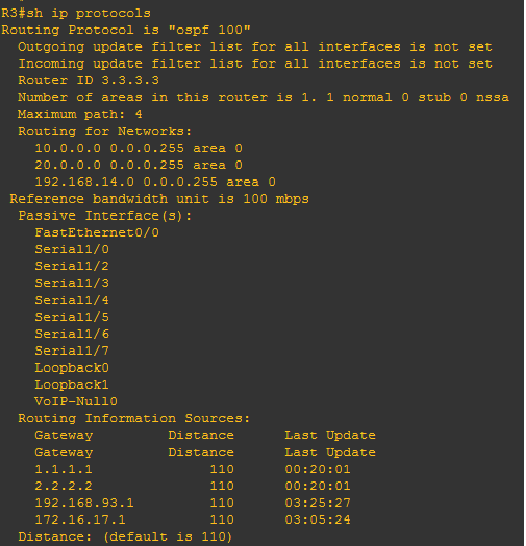
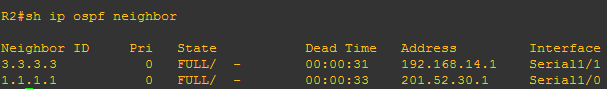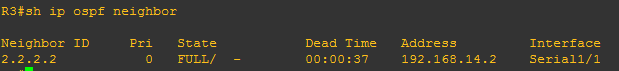Hi mate! We’re back again and we’re getting more serious. We have to grasp more on OSPF operation and hopefully I will be able to explain it on the simplest manner. Title above focus on OSPF tables. There are just three tables that we have to remember on OSPF namely: neighbor table, ip routing table and lastly Link State Database LSDB table.
A.) Neighbor table
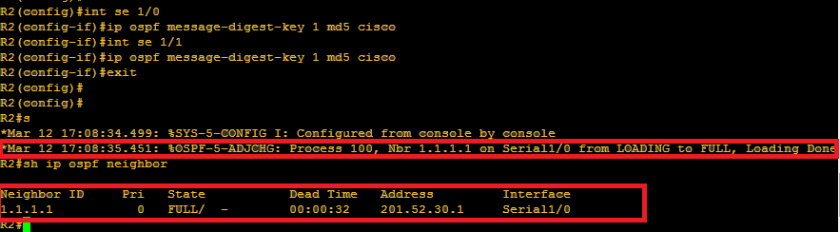
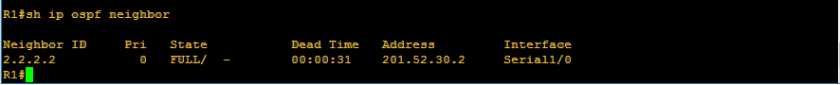
Verifying command: show ip ospf neighbor
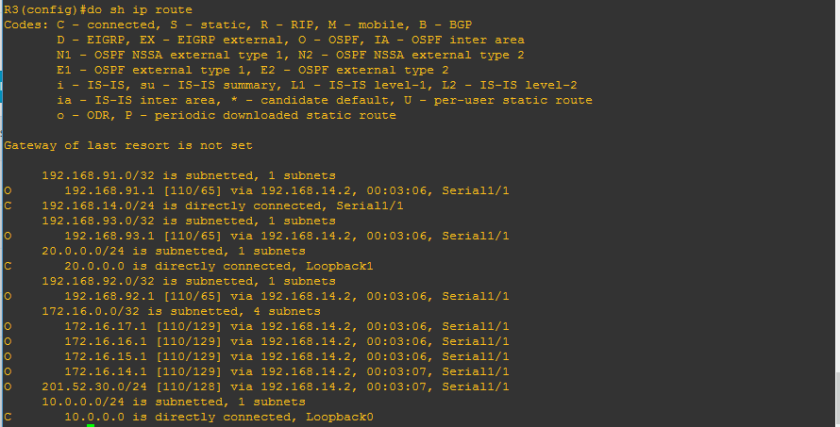
Do you happen to remember this ?
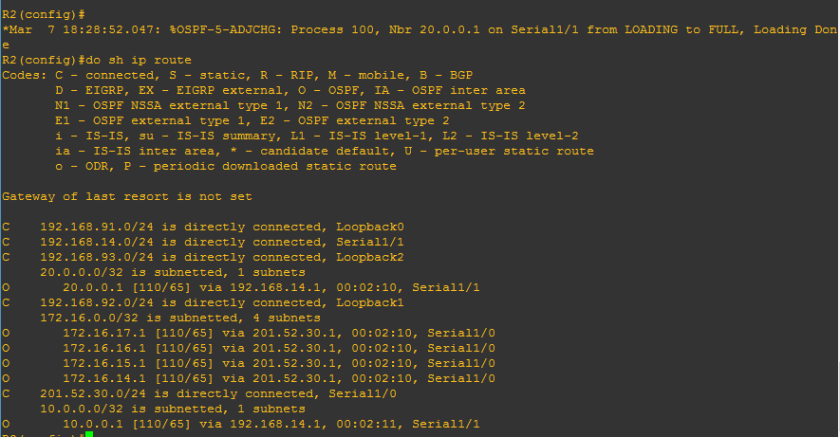
Yup, we have already encountered already the neighbor table. So we can conclude that the OSPF table includes the router-id of the neighbor routers, priority set on each neighbor which we will deal further as we go on, the OSPF stage which we will discuss as well later and interface of the neighbor router where the local router is connected and the ip address itself. Too wordy right? Lemme discuss the OSPF neighbor content one by one.
1.) Neighbor router’s Router-id – the identifier of the neighbor router that also sends OSPF updates
2.) Neighbor router’s priority – this is used on the election of DR and BDR routers. We will go further on the classification of ospf routers, it seems like there will be slave and master routers somewhat like that but I cannot provide more details about this without getting unto the basic of OSPF operation.
3.) OSPF stage – the word ” FULL” is the final stage on the OSPF stages on establishing neighbor adjacency. We will have a separate discussion about that
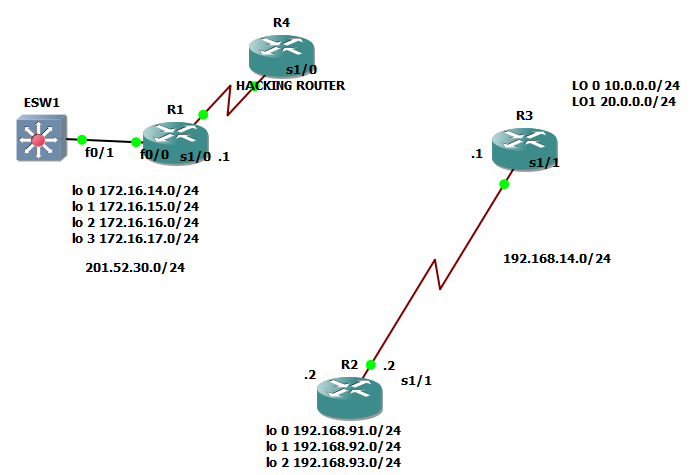
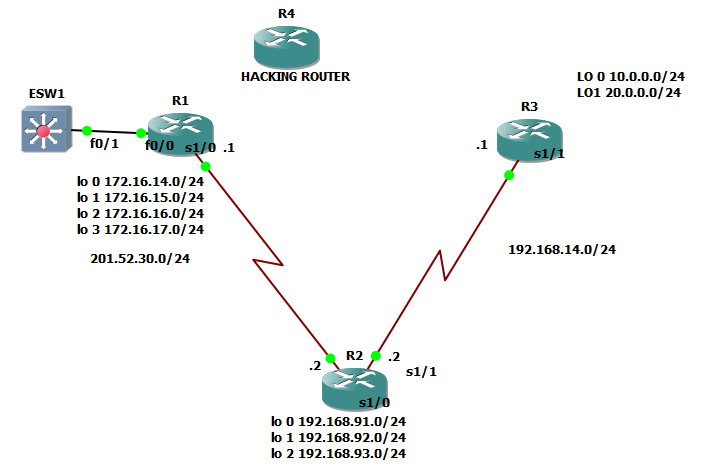
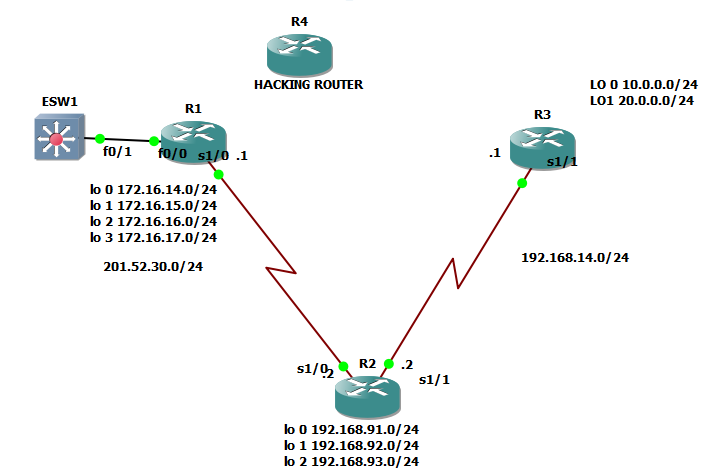
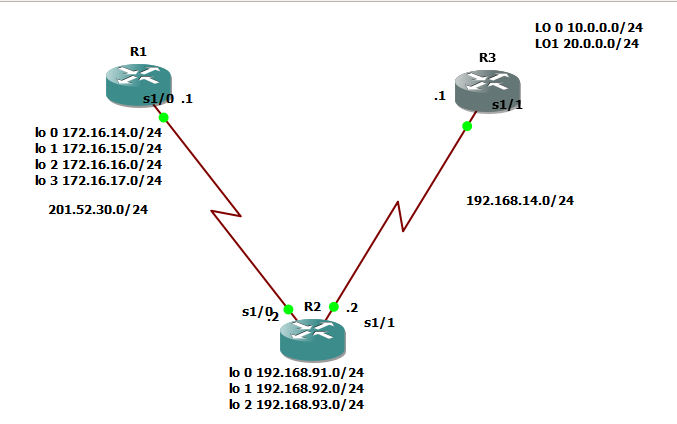
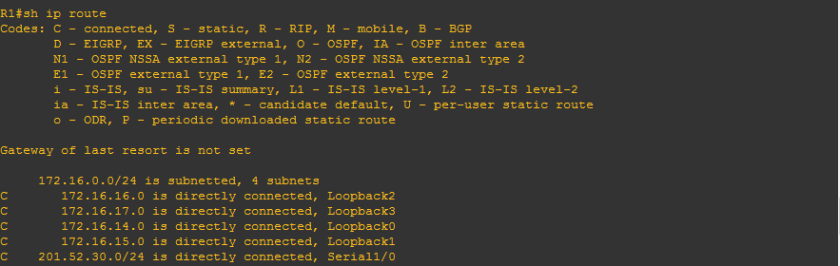
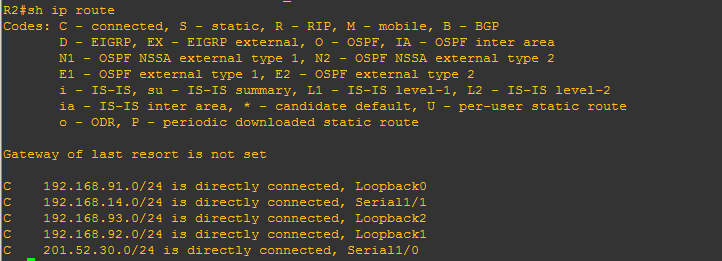
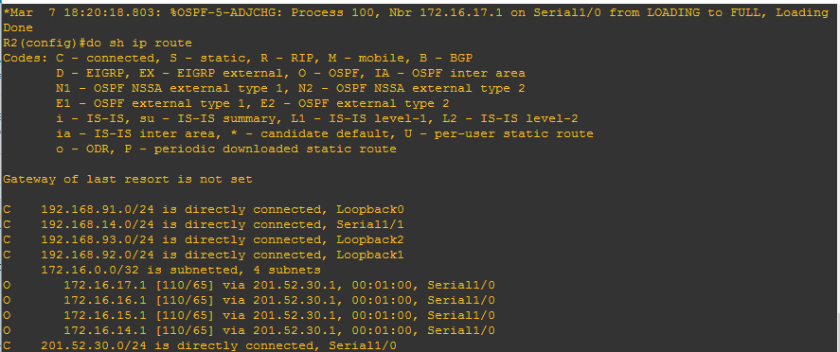
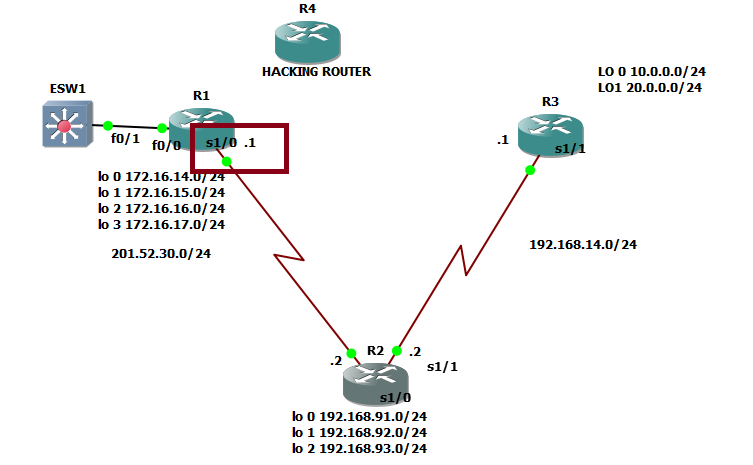
4.) The IP address of the neighbor router exiting interface. We just used the same network topology we used on the previous OSPF topic and as you can see below:

The squared ones are those the interface of the neighbor routers of R2 and also covers the IP addresses 201.52.30.1 and 192.168.14.1
5. Interface of the neighbor routers- these are source of the OSPF updates
B.) IP routing table
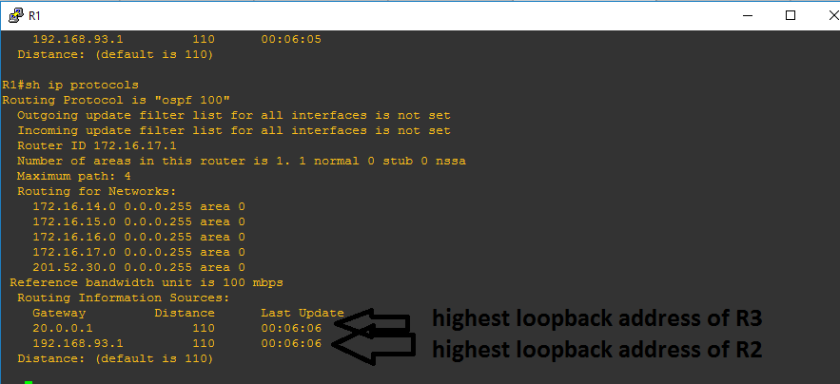
Verifying commands: show ip route, show ip route ospf
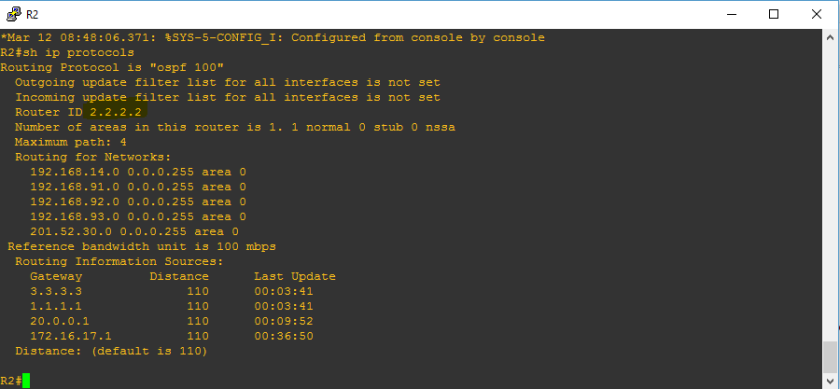
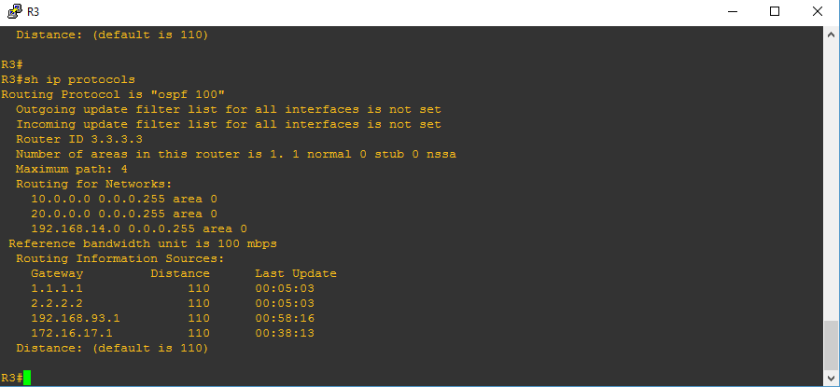
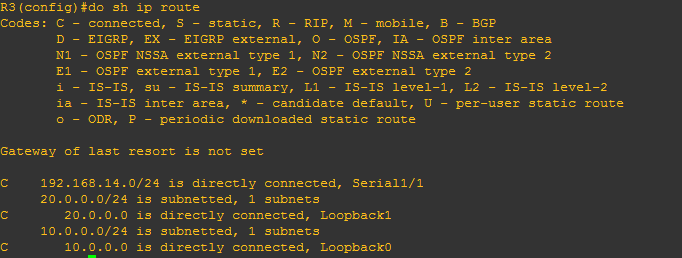
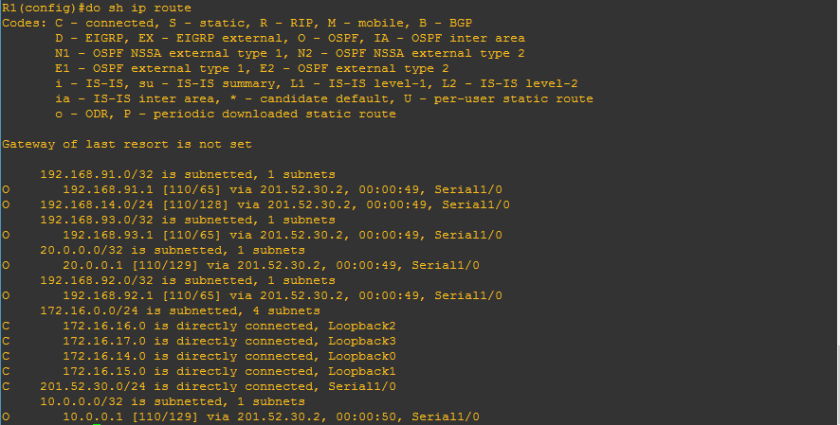
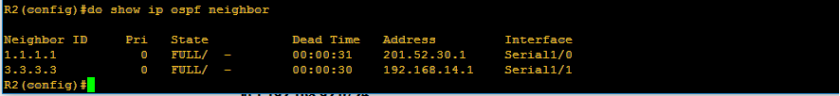
I hope that I was able to help you to read routing table. It’s just very easy as there was a legend to follow what protocols appearing below. “O” on the ip routing table represents the OSPF protocol. Below is a sample of routing table of R2 on the network topology.
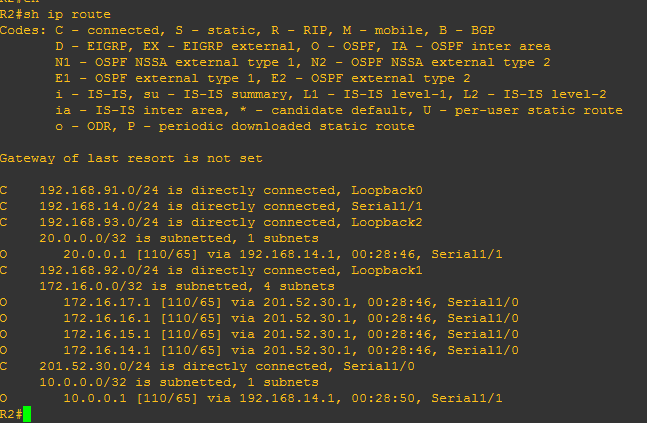
To show only OSPF on the routing table, use show ip route ospf
C.) Link State Database (LSDB) table
First, let us define Link- State, link-state is just one of the routing protocol according to algorithm. Algorithms that I am telling you are those like distance vector, link state and hybrid protocols. The reference to define its metrics is the cost. Cost has computation equivalent to reference bandwidth over point to point bandwidth. The usual reference bandwidth is 100 kbps. So cost = 100 kbps / link bandwidth.
Anyway, we forgot our goal which is to define link state. Link refers to the interface and so link state refers to the status of the interface. Therefore we conclude that LSDB is a database of the status of the interfaces. However, that is just the layman’s term explanation to define LSDB.
Below is an image that shows the content of LSDB.
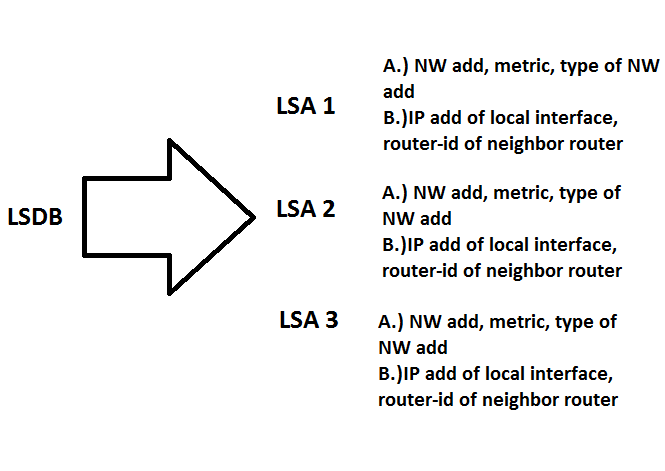
Alright, another term rise that makes the study confusing but you don’t have to worry about that.Lemme define them one by one.
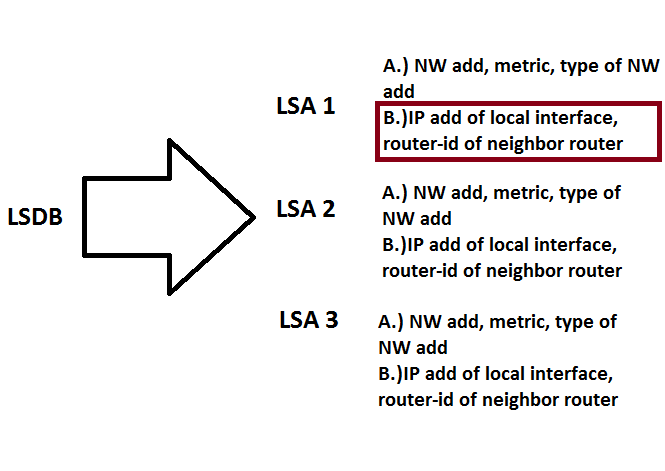
LSDB – technically is a database of LSA’s or link state advertisement.
LSA – contains the information of the interface like network address, metric, type of network address etc. These are the information advertised by the interface once the network command was activated.

So let us discuss the content of LSA. I indicate on the the white image above that there is option A and B. Those are actually categories of link state. Link state categories are A.) what’s with the interface — network address, metrics, type of network address and B.) is there router connected? –> ip address of neighbor router and router-id of neighbor router.
Let us try to check these LSAs by examining our original network topology.
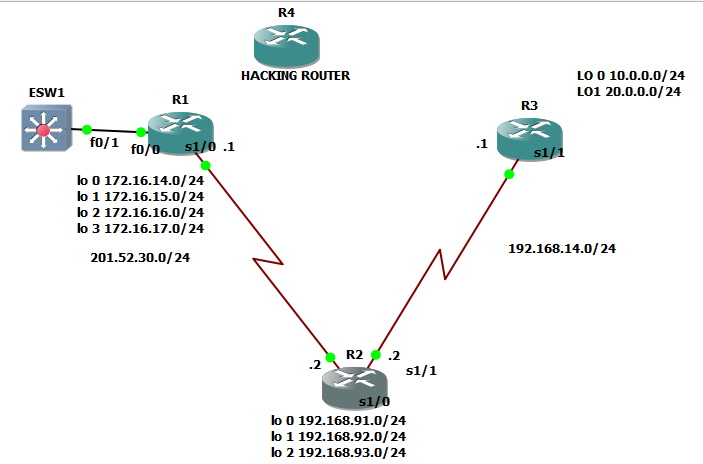
Let us check the LSA of R2
Category A for interface from R2 to R1 ( what’s with the interface)
Network address:201.52.30.0 /24
Metric:since we don’t know the metric, let us check the speed of the link, by running command ” sh interfaces se 1/0″ since it is interface se 1/0
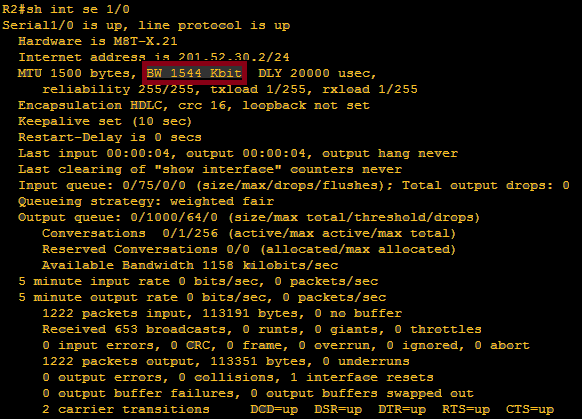
We can see that is 1544 kbps so definitely the cost or the metric is 100/1.544 = 64.766 and we can round it down to 64
Metric:64
Type of Network address:
There area two types of network address that we have to define;
a.Stub network- these are loopback address network, network of which interface has only one or no router connected on the other end
b. Transit network- network which interface has two or more routers connected
Since the interface that we are talking about is serial 1/0 and since it is only connected with one router which is connected to a switch, we conclude that it is a stub network.
Type of Network address:Stub network
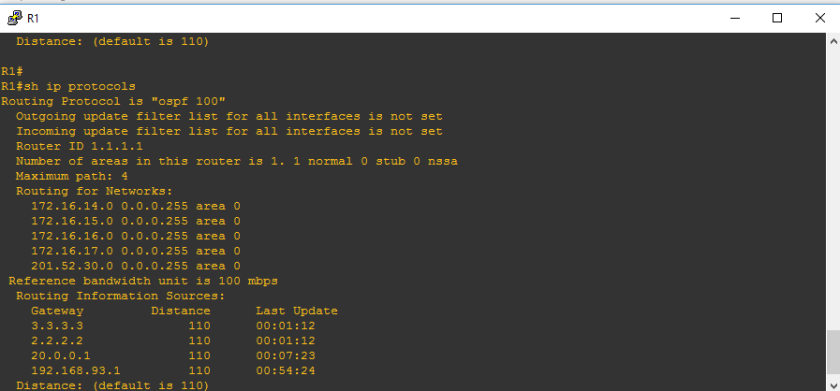
Let us try to verify the LSA on LSDB using this commands:
show ip ospf database
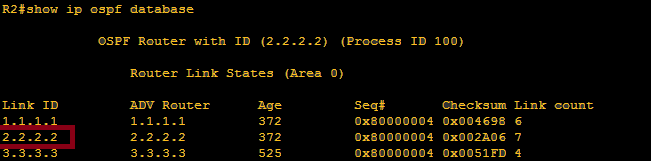
Highlighted on the above image is link id 2.2.2.2 because on area 0 on router 2, we got three LSA’s namely 1.1.1.1, 2.2.2.2 and 3.3.3.3. Since we would like to check the interface of router 2, we need to further check the content of LSA of link-id 2.2.2.2 by verifying command: show ip ospf database router 2.2.2.2
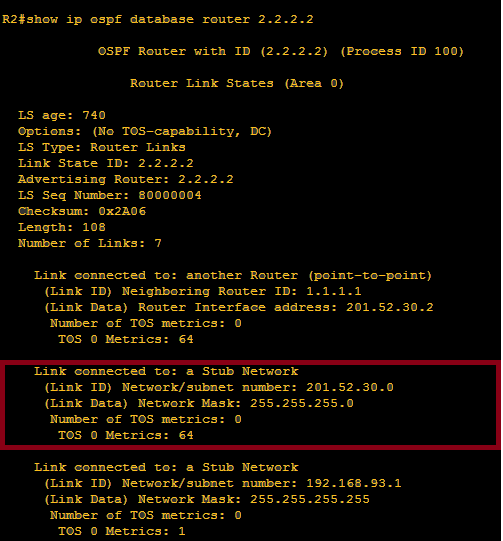
Honestly, there should be 7 links but I only highlighted above the interface that we checked its LSA content. So let us try to check ” what’s with the interface?”
We got type of network as stub network, network address of 201.52.30.0 255.255.255.0 and metric of 64. There dyou go! we are able to check one of link state categories which asks what’s with the interface?
Let us try to check the 2nd link state category which asks ” is there a router connected?”
Yes, there is a router connected, and let us check the interface of router 1 that links to router 2 and it is the serial 1/0 of R1. So I just would like to clarify here that on a certain LSA of a router, we will see as well the state of the interface of neighbor router that provides OSPF update.
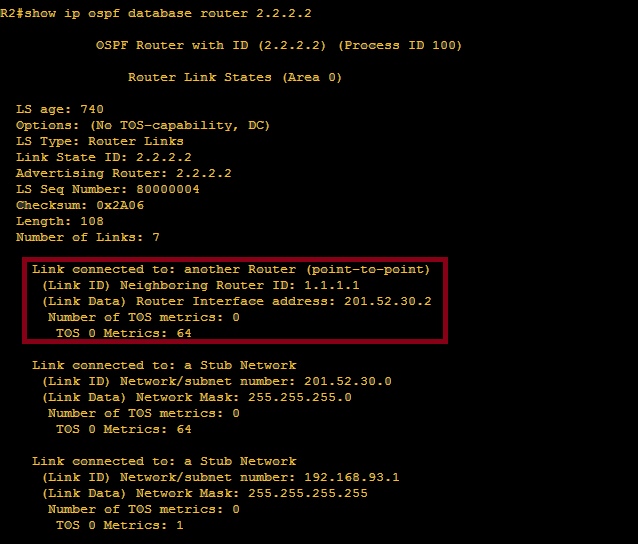
We need to define the IP address of local interface , local interface means the interface of the original router that we are working with, which is R2. so it must be 201.52.30.2
IP add of local interface: 201.52.30.2
Also, we need to verify the router-id of the neighbor router, in our case, it must be R1. So,
Router-id of neighbor router:1.1.1.1
Let us try to verify:
Oh yeah! That’s all for now for the OSPF tables. Talk to you later!